SPE1.1.0.2
ENCRYPT SELECTED PACKAGE
CONTENTS
DESCRIPTION
File packet encryption is the process of encrypting files whose information is recorded in the packet if they are available and physically accessible.
Encrypting file packages is fundamentally different from encrypting selected files and folders. In practice, it is more of a process that is an automatic execution of a meta-script. Packet encryption automatically checks the file before any actions are taken. When encrypting selected files, this process is recommended and its implementation depends on the operator's choice.
Unlike the encryption of selected files, with the encryption of packages, it is possible that the files are not located on one physical medium, but on several such ones, including and external.
When encrypting files, the information about which is stored in the file package (metadata about the file) is not actually encrypting the contents of the package, but encrypting the physical files. This process is only possible if the files are available and physically accessible.
It is important to understand this specificity, especially in cases where files located on one or more external devices are encrypted, including network or file servers.
PROTECTION MODE
The protection mode is a hybrid component that determines how the crypto mechanism (or the mechanisms) will be formed within the working session.
By "session" we will mean the encryption or decryption process of the files in the selected package.
Before proceeding with the encryption of file packages, it is necessary to determine what encryption mode will be used.
The different encryption modes use for different data encryption models.
If there is a difference between the mode used to encrypt the files in the packages and the one used to decrypt them, some or all of the files may be irreparably damaged.
Hybrid encryption modes are an extremely useful tool when building enterprise information protection solutions. In practice, they minimize the probability of critical information to be accessible out of the controlled perimeter where it is stored, even by individuals with super administrator access. This significantly improves the efficiency of DLP systems using this technology.
The protection modes used in FPM are as follows:
- Standard Protection Mode, SPM - In this mode, all files in the package will be encrypted using the cryptographic primitives selected in the file encryption mechanism formation module.
- Package Protection Mode, PPM - In this mode, the files encryption will be performed based on the crypto primitives recorded in the e-notebook for the selected package.
- Hybrid Protection Mode, HPM - The hybrid encryption mode assumes that each file can be encrypted using a specific set of crypto primitives. In this case, the information is stored in the file package.
Note: More about security modes can be found in the encryption section, as well as in the specialized documentation.
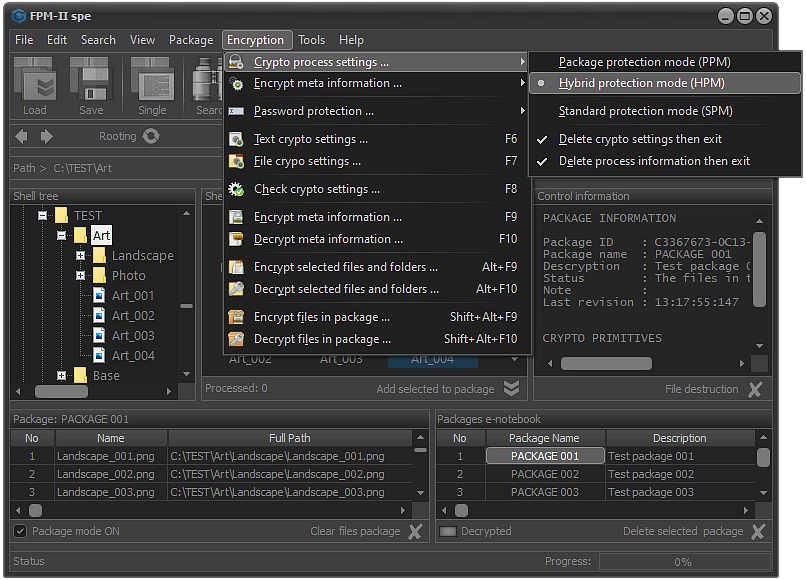
Fig.1. Select protection mode.
ENCRYPT SELECTED PACKAGE
The standard process of encrypting package files and folders converts the list of files, included in package, into a form that prevents unauthorized access.
In FPM, this process is implemented using a combination of crypto primitives, including a cipher algorithm, crypto mode, hash function, cipher IV, hash salt, user password, etc.
Before proceeding with the encryption of selected files and folders, the system must turn on the batch processing mode. For this purpose, the check box located in the lower left corner of the application, immediately below the table with the contents of the file packages, must be set to Package mode ON.
Only after batch mode is turned on can the package files and folders will be encrypted.
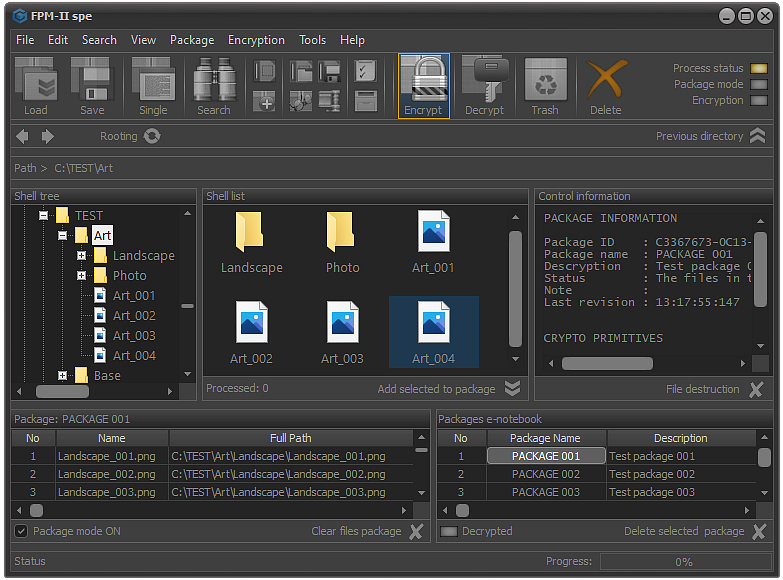
Fig.2. Start encryption process.
In order to encrypt selected package, it is necessary to select Encryption - Encrypt files in package from the main menu or use the keyboard shortcut Shift+Alt+F9.
Another option is to use the Encrypt button located on the control panel.
As a result of these actions, the process of encrypting the files whose information is recorded in the selected package will be started without affecting the contents of the package in any way.
Note: In the standard versions of the application, the selection of files to encrypt is done only for selected package.
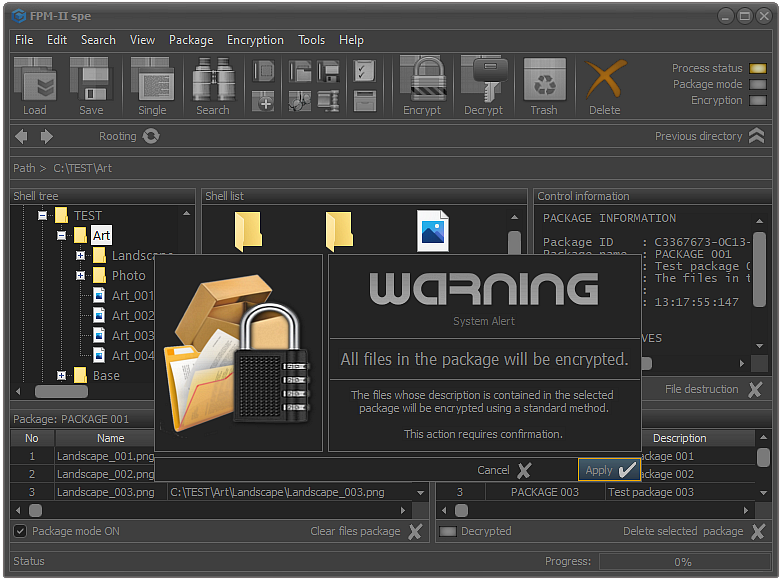
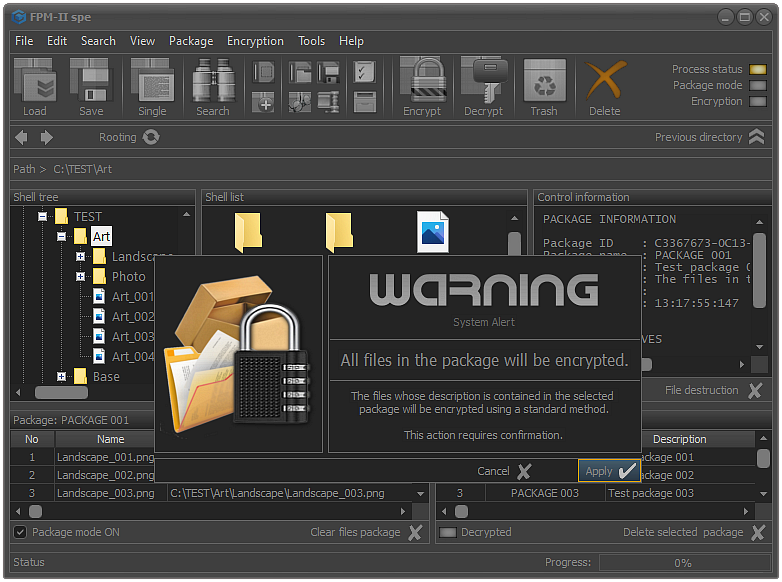
Fig.3. Encryption confirmation.
Before proceeding with the encryption of the files from the selected package, it is necessary to confirm the process.
The reason for asking for confirmation is that the operator does not always see in the shell list the files that are contained in the package. Unlike other forms of encryption here, any form of emergency termination is undesirable. It is also a good idea to check whether access to each of the files contained in the package is guaranteed. If such access is missing, the files will not be encrypted. Although the application will reflect this in the system report, it is possible for the operator to ignore the warnings and at a later stage try to decrypt files that were not encrypted, which is unacceptable.
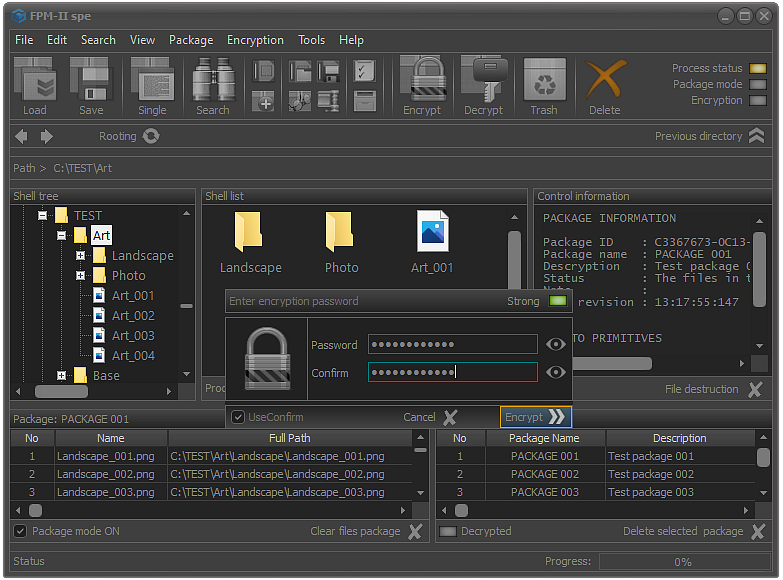
Fig.4. Enter encryption password.
After the package is selected and the encryption process confirmed, the screen will display the specialized module for entering the user password as shown in the image.
It is important to know that the user password is not directly related to the encryption process. The password serves only to authorize the user. Even if the password is not entered, if the process is not terminated by clicking the Cancel button or using the Esc key, the files in selected package will be encrypted.
To confirm the encryption, it is enough to click the Encrypt button or use the Enter key.
The execution of the encryption process will be reflected by the application. The duration will depend on both the number of files in the package and their size and the cryptographic primitives used.
Note: It is recommended to run several tests with the File Encryption Mechanism Selector module before proceeding with file packet encryption.
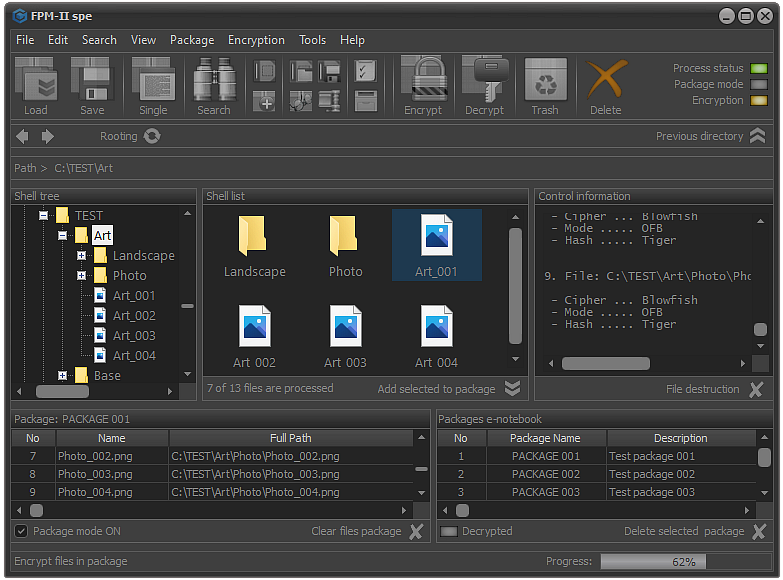
Fig.5. Encrypt the files in the selected package.
If the encryption process has passed without any errors, the system will display a message about the successful completion of the encryption of the files in package.
Once the files are encrypted, they will not be viewable until the decryption process is performed. Also, as a result of encryption, changes will occur to the CRC and hash function of the files in selected package.
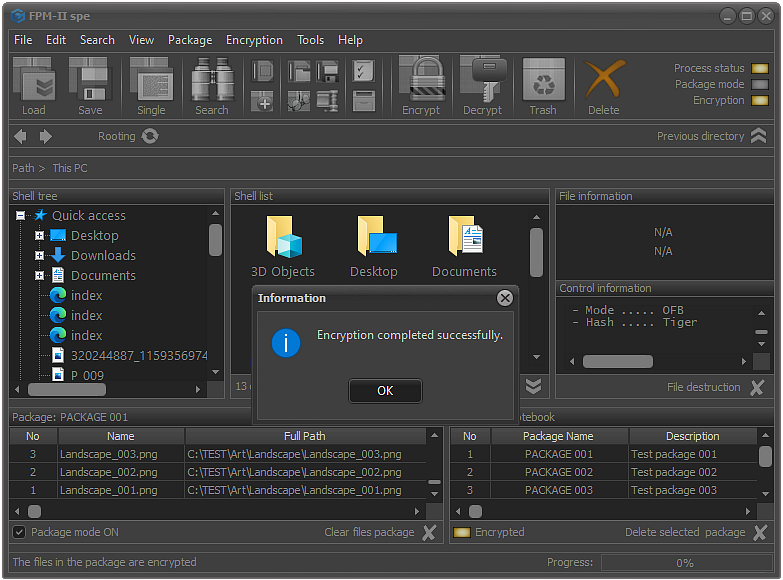
Fig.6. Finishing the process of encrypting the file package.
If the encryption process has passed without any errors, the system will display a message about the successful completion of the encryption of the selected file package.
Once the files are encrypted, they will not be viewable until the decryption process is performed. Also, as a result of encryption, changes will occur to the CRC and hash function of the file.
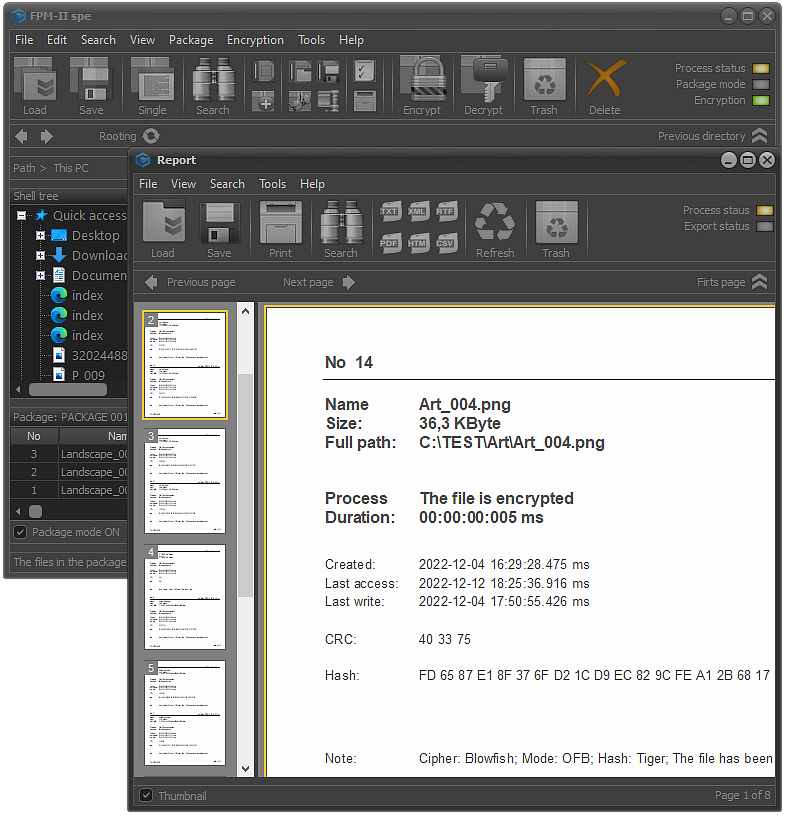
Fig.7. Package encrypting system report.
The parameters of the encryption process of the files in the package will be recorded in a system report.
Documentation is an important component of the file packet processing process because it ensures that subsequent decryption will be performed correctly.
In order to ensure security, system reports do not contain information directly related to components such as secret keys and user passwords.
DECRYPT SELECTED PACKAGE
The decryption process of the files in selected package converts them back to the way they were before they were encrypted.
The decryption process of the files in selected package converts them back to the way they were before they were encrypted.
In order to perform decryption when standard mechanisms are used, it is necessary that the selected crypto primitives are absolutely identical to those used in the encryption process.
If only one of the crypto primitives is distinguished the files will not be restored to their original form.
Before starting the decryption process, we need to be sure that the files are encrypted and that we have all the necessary information to configure the decryption mechanism.
Once the crypto mechanism is configured, the process itself can be executed.
Note: In all versions of the product that use an e-notebook, there is a field that reflects the status of the package. If the package is encrypted, in addition to the entry in the status field, this will also be reflected by the light indicator located in the lower left corner of the workbook field.
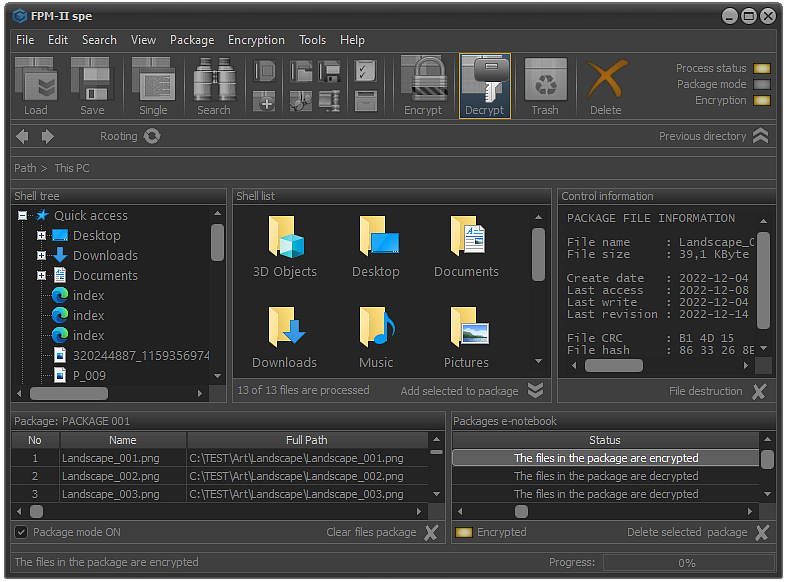
Fig.8. Start package decryption process.
In order to decrypt selected package, it is necessary to select Encryption - Decrypt files in package from the main menu or use the keyboard shortcut Shift+Alt+F10.
Another option is to use the Decrypt button located on the control panel.
As a result of these actions, the process of encrypting the files whose information is recorded in the selected package will be started without affecting the contents of the package in any way.
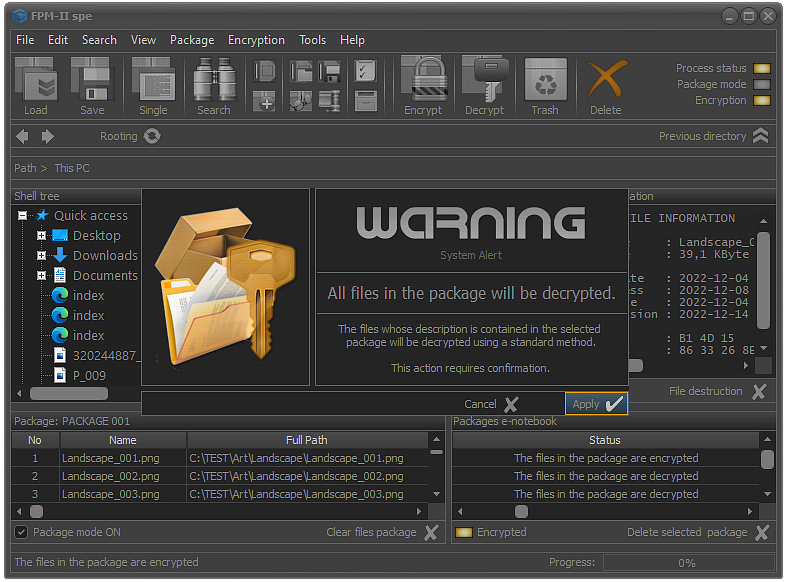
Fig.9. Confirming the selected package decryption.
Before proceeding with the decryption of the files from the selected package, it is necessary to confirm the process.
Requiring confirmation prevents the possibility of accidentally decrypting a file package. This is an element of the user error protection system.
It is necessary to keep in mind that FPM is a professional digital data encryption system. This assumes a good knowledge of encryption processes or a good understanding of general and specialized application functionality.
Note: The decryption process is critical and requires a careful approach by the operator.
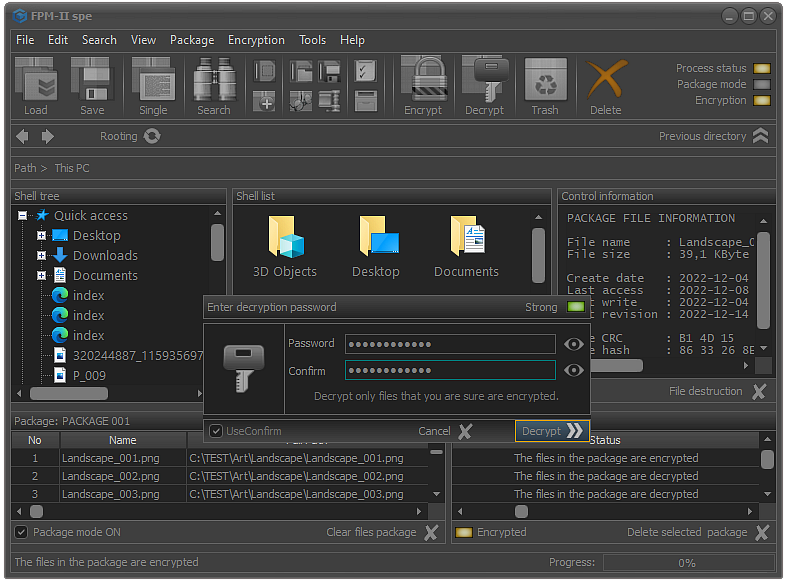
Fig.10. Completing the decryption process.
After the package is selected and the decryption process confirmed, the screen will display the specialized module for entering the user password as shown in the image.
Even if the password is not entered, if the process is not terminated by clicking the Cancel button or using the Esc key, the files in selected package will be decrypted.
To confirm the decryption, it is enough to click the Decrypt button or use the Enter key.
The execution of the decryption process will be reflected by the application. The duration will depend on both the number of files in the package and their size and the cryptographic primitives used.

Fig.11. Completing the decryption process.
If the decryption process has passed without any errors, the system will display a message about the successful completion of the decryption of the selected files in package.
After the decryption of the selected file package is completed, the files will not only be restored to their original form and usable, but their CRC and hash functions will be identical to the original ones. This is one of the criteria that allows not only to control the decryption process, but is also a basic criteria for whether any changes have been made to the files.
Contents