SPE1.1.0.2
STANDARD FUNCTIONS
CONTENTS
- File encryption
- Key Derivation Function
- Standard protection mode (SPM)
- Package protection mode (PPM)
- Hybrid protection mode (HPM)
FILE ENCRYPTION
File encryption transforms data into code that only authorized users can decipher, preventing unauthorized users from being able to access, view, and understand sensitive information.
With data breaches and identity theft on the rise, encrypting files not only means protecting an organization’s reputation and trustworthiness — it means protecting people and their valuable assets.
File encryption is also a key pillar of cybersecurity, with national and global policies requiring its use.
The California Consumer Privacy Act of 2018 (CCPA),
the US’s Healthcare Insurance Portability and Accountability Act (HIPAA),
the EU’s General Data Protection Regulation (GDPR),
and Canada’s Federal Information Processing Standards (FIPS) are just a few of many regulations setting standards and guidelines for sufficient file encryption.
File encryption is helpful if a user needs to send individual files securely over the internet or store them on a removable device such as a USB stick. A file in transit is sometimes referred to as data in motion.
FPM uses symmetric encryption algorithms to encrypt files, but unlike other standard solutions, instead of exchanging secret keys, systems for forming session crypto mechanisms are used.
In turn, the crypto mechanisms are the ones that generate the secret keys needed to encrypt or decrypt the selected files. Cryptomechanisms are a set of proven cryptographic primitives united in a common functional mechanism. This approach allows avoiding the disadvantages of symmetric forms of encryption while preserving their advantages.
Much better solutions are to use object-relational forms of file encryption, as well as control strings, which are the subject of separate considerations.
Note: Much better solutions are to use object-relational forms of file encryption, as well as control strings, which are the subject of separate considerations.
KEY DEVIATION FUNCTIONS
Кey derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher).
KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES.
The original use for a KDF is key derivation, the generation of keys from secret passwords or passphrases.
Variations on this theme include:
- In conjunction with non-secret parameters to derive one or more keys from a common secret value (which is sometimes also referred to as "key diversification"). Such use may prevent an attacker who obtains a derived key from learning useful information about either the input secret value or any of the other derived keys. A KDF may also be used to ensure that derived keys have other desirable properties, such as avoiding "weak keys" in some specific encryption systems.
- As components of multiparty key-agreement protocols. Examples of such key derivation functions include KDF1, defined in IEEE Std 1363-2000, and similar functions in ANSI X9.42.
- To derive keys from secret passwords or passphrases (a password-based KDF).
- To derive keys of different length from the ones provided: one example of KDFs designed for this purpose is HKDF.
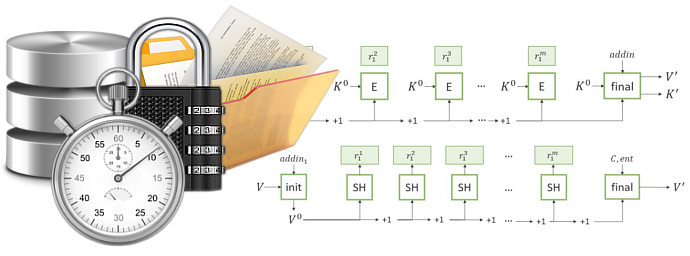
STANDARD PROTECTION MODE (SPM)
In the standard protection mode, all files whose information is stored in the file package are encrypted using a predefined set of cryptographic primitives (crypto mechanism), which means that the same session secret key will be generated for each file.
The standard methd is identical to the mechanism used to encrypt selected files and folders, but in this case the list of files to be encrypted or decrypted is formed by the entries in the selected file package.
In this case, the configuration of the cryptographic mechanism is performed by the operator, and the parameters are set in the specialized module (section: Crypto Primitives Management).
What is important to know is that the information written in the electronic notebook and in the file package, related to the crypto primitives used, will be ignored.
The advantage of this method is its high productivity. The disadvantage is that the same encryption mechanism is used for each file in the package.
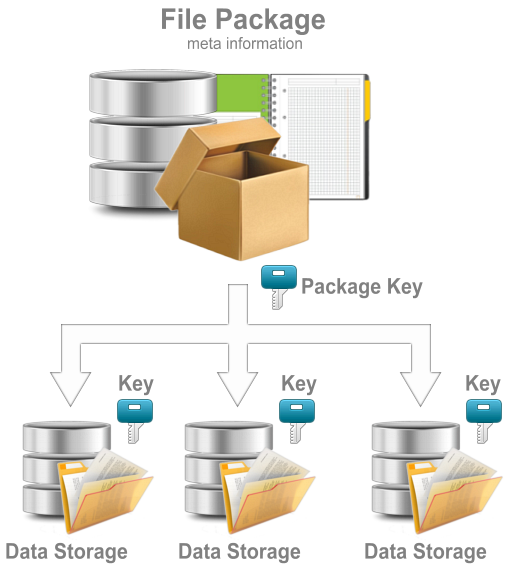
Fig.1. Standard protection mode.
PACKAGE PROTECTION MODE (PPM)
In package protection mode, the files whose information is stored in the file batch are encrypted using an encryption mechanism that is generated using the cryptographic primitives written in the batch for each file.
This means that it is possible for individual files and/or groups of files to be encrypted with different secret keys and to use different crypto primitives.
Unlike the standard security mode, here the session cryptomechanism is formed based on the information about the standard crypto primitives recorded in the file package.
In this case, the cryptomechanism information contained in the Crypto primitives management module will be ignored. However, this does not mean that this information cannot be written into the packet and used in the encryption process. The choice to do so is left to cyber security professionals.
This method has a lower performance than the standard one, but with an appropriate configuration of the crypto primitives, it will guarantee a much higher degree of protection.
Note: If the same combination of crypto primitives is specified for each file saved in the file package, we will have a result identical to that of standard encryption.

Fig.2. Package protection mode.
HYBRID PROTECTION MODE (HPM)
In hybrid encryption mode, the files whose information is stored in the file package are encrypted using a modified encryption mechanism. This mechanism not only forms a session cryptographic mechanism for each file, but also chooses how the secret key is generated.
This method is a variation of object-relational encryption. The difference is that the numeric object or control string is replaced by a function that selects how the session secret key will be generated.
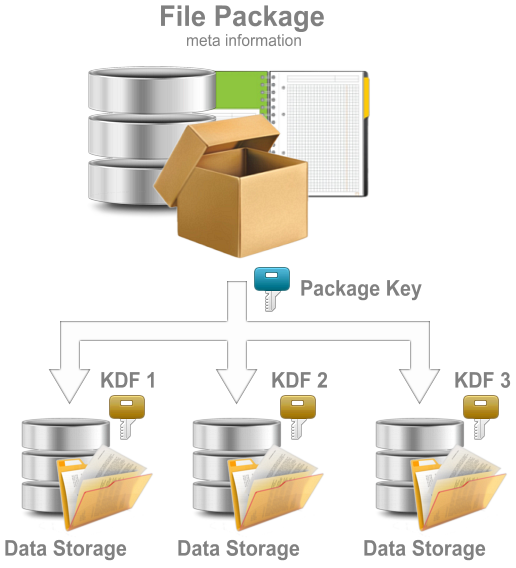
Fig.3. Hybrid protection mode.
We can assume that in practice this is the file packet encryption method that guarantees the highest possible degree of protection. The main advantage is that the mechanism of choosing cryptographic primitives remains hidden from the user. In practice, this ensures that even operators with super administrator rights will not be able to access the secret parameters of the mechanism used.
This choice allows the method to be used as an element of specialized protection, preventing "inside attacks".
The execution speed of the processes does not significantly differ from the previous methods. If there is a delay it is minor and it is in the part preceding the processing of the files.
The selection of the protection method is done by selecting Encryption - Crypto process settings from the main menu, as shown in the image.

Fig.4. Select protection mode..
Contents