SPE1.1.0.2
ENCRYPT SELECTED FILES AND FOLDERS
CONTENTS
DESCRIPTION
Encryption of selected files and folders is a process where user-selected files and folders are encrypted using a pre-selected cryptographic mechanism.
In standard file and folder encryption methods, the crypto mechanism consists of a set of highly reliable cryptographic primitives.
Hybrid and object-relational use additional key files, control strings, etc. digital components that described in the specialized sections of the File Protect System (FPS) application.
Advanced and hybrid encryption methods for selected files and folders are available in FPS versions higher than FE. It should not be forgotten that the main function of the FPM is related to the processing (encryption) of the contents of file packages. In practice, this means that selective encryption is more of an auxiliary character.
STANDARD ENCRYPTION
The standard process of encrypting selected files and folders converts the files into a form that prevents unauthorized access.
In FPM, this process is implemented using a combination of crypto primitives, including a cipher algorithm, crypto mode, hash function, cipher IV, hash salt, user password, etc.
Before proceeding with the encryption of selected files and folders, the system must turn off the batch processing mode. For this purpose, the check box located in the lower left corner of the application, immediately below the table with the contents of the file packages, must be set to Package mode OFF.
Only after batch mode is turned off can the selected files and folders will be encrypted, otherwise, encryption will be done against the file packets.
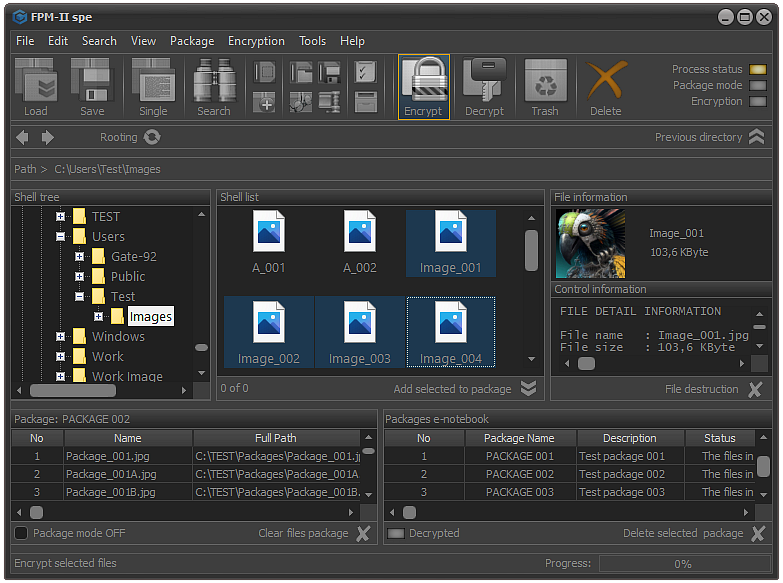
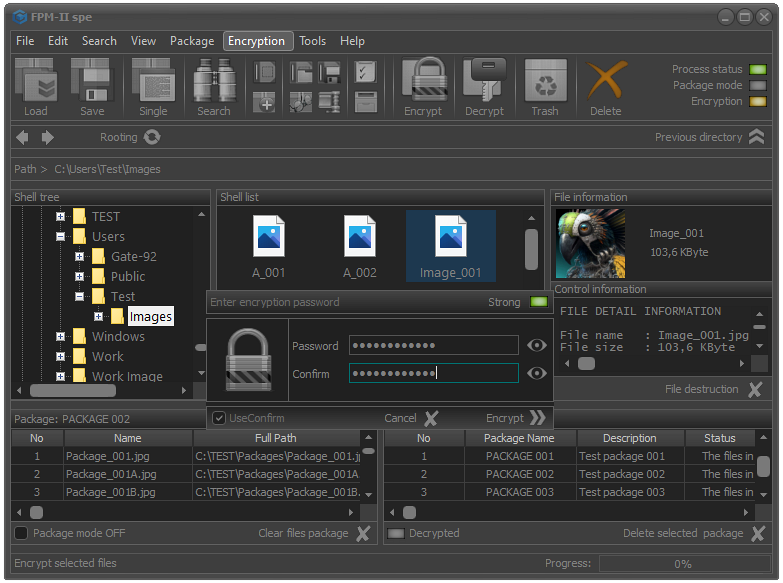
Fig.1. Select files to encrypt.
In order to encrypt selected files, it is necessary to select Encryption - Encrypt selected files and folders from the main menu or use the keyboard shortcut Alt+F9.
Another option is to use the Encrypt button located on the control panel.
If there are no files and folders selected in the Shell list field, the system will automatically display a message that there are no files selected to be encrypted.
Note: In the standard versions of the application, the selection of files to encrypt is done only in the shell list field and nowhere else.
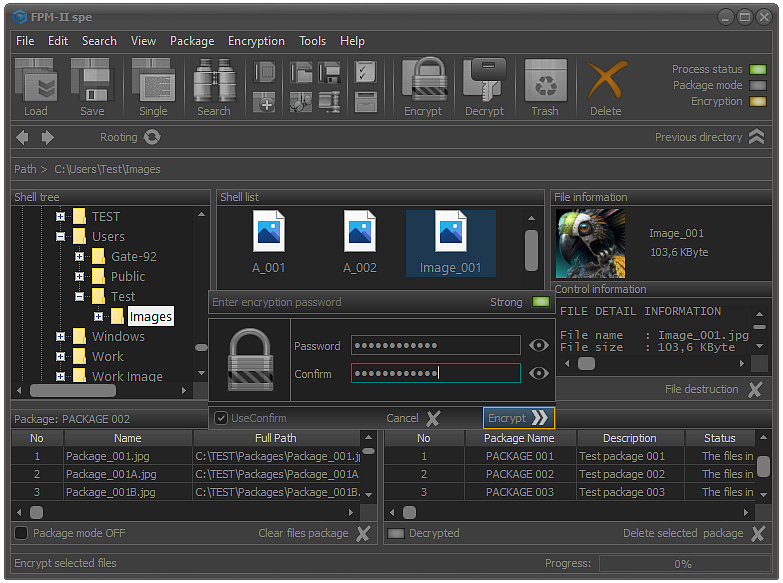
Fig.2. Entering a user password.
After the files are selected and the encryption process started, the screen will display the specialized module for entering the user password as shown in the image.
It is important to know that the user password is not directly related to the encryption process. It serves only to authorize the user. Even if the password is not entered, if the process is not terminated by clicking the Cancel button or using the Esc key, the selected files and folders will be encrypted.
To confirm the encryption, it is enough to click the Encrypt button or use the Enter key.
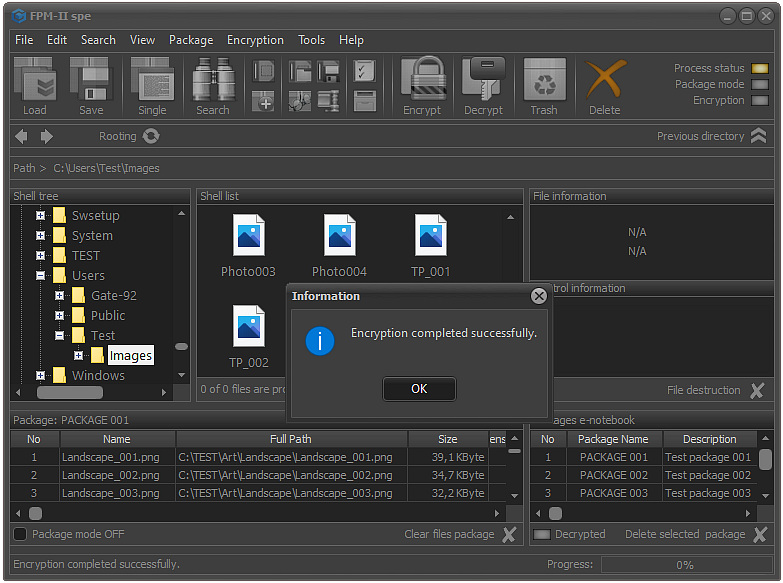
Fig.3. Completing the encryption process of selected files.
If the encryption process has passed without any errors, the system will display a message about the successful completion of the encryption of the selected files and folders.
Once the files are encrypted, they will not be viewable until the decryption process is performed. Also, as a result of encryption, changes will occur to the CRC and hash function of the file.
Example:
Let's compare the information about Image_001.jpg file before and after encryption.
From the control panel for setting file encryption parameters, we select the following crypto primitives as follows:
Hash Salt and Cipher ID are generated by the system randomly.
The parameters of the file before and after encryption are as follows:
FILE DETAIL INFORMATION
| Property | Value |
|
File name |
Image_001.jpg |
| File size | 103,6 KByte |
| File path | C:\Users\Test\Images\ |
| Root | C:\ |
| Create date | 2022-12-15 12:51:38.134 ms |
| Last access | 2022-12-16 13:24:17.029 ms |
| Last write | 2022-12-16 13:24:15.988 ms |
| File CRC 8 | B6 |
| File CRC 16 | DE 43 |
| File CRC 32 | DA 8D 35 |
| File CRC 64 | A4 33 AE 28 |
| File hash | 32 80 4F D0 77 7B B3 CF CB 96 72 21 42 A0 90 44 6E A6 FC ... |
FILE DETAIL INFORMATION
| Property | Value |
|
File name |
Image_001.jpg |
| File size | 103,6 KByte |
| File path | C:\Users\Test\Images\ |
| Root | C:\ |
| Create date | 2022-12-15 12:51:38.134 ms |
| Last access | 2022-12-16 13:23:10.740 ms |
| Last write | 2022-12-16 13:21:01.450 ms |
| File CRC 8 | B3 |
| File CRC 16 | B2 C1 |
| File CRC 32 | 62 99 84 |
| File CRC 64 | B2 FA 5A 09 |
| File hash | FB 1C A9 BE 12 13 AE 5F 7B 3F EE 21 AF 21 7A 29 B4 15 EE ... |
As can be seen from the obtained results, the changes are in the CRC and the hash function of the file. All other metrics are kept as they were before the file was encrypted.
STANDARD DECRYPTION
The decryption process of selected files and folders converts them back to the way they were before they were encrypted.
In order to perform decryption when standard mechanisms are used, it is necessary that the selected crypto primitives are absolutely identical to those used in the encryption process. If only one of the crypto primitives is distinguished the files will not be restored to their original form.
Before starting the decryption process, we need to be sure that the files are encrypted and that we have all the necessary information to configure the decryption mechanism.
Once the crypto mechanism is configured, the process itself can be executed. In order for the process to start, there needs to be at least one selected file or folder that will be decrypted.
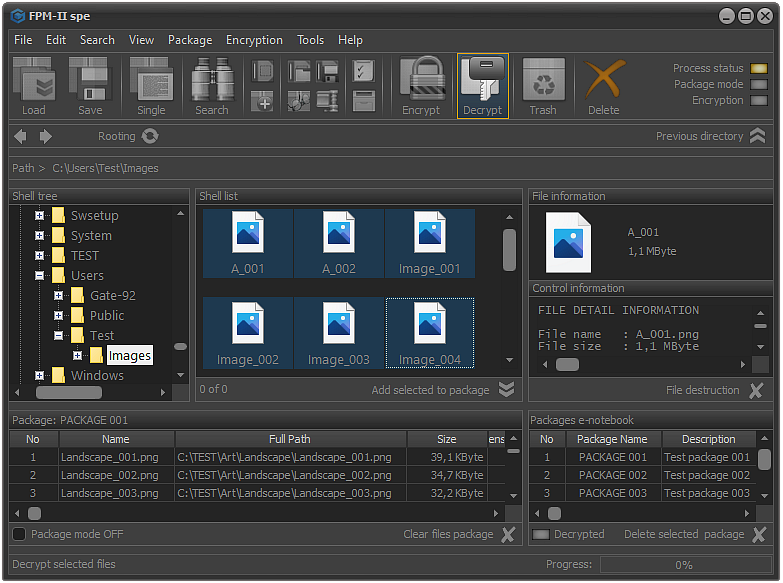
Fig.6. Files and folders decryption.
In order to decrypt selected files, it is necessary to select Encryption - Decrypt selected files and folders from the main menu or use the keyboard shortcut Alt+F10.
Another option is to use the Decrypt button located on the control panel.
If there are no files and folders selected in the Shell list field, the system will automatically display a message that there are no files selected to be decrypted.
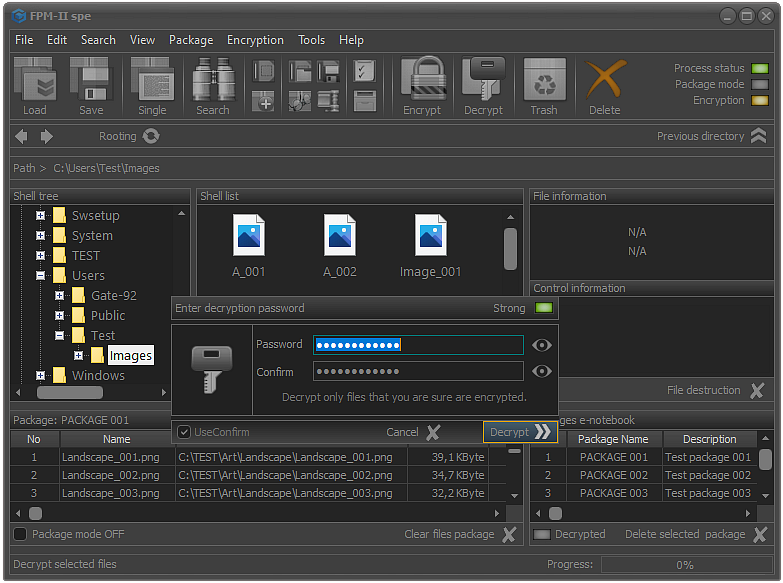
Fig.7. Decryption password entering.
After the files are selected and the decryption process started, the screen will display the specialized module for entering the user password as shown in the image.
It is important to know that the user password is not directly related to the decryption process. It serves only to authorize the user. Even if the password is not entered, if the process is not terminated by clicking the Cancel button or using the Esc key, the selected files and folders will be decrypted.
To confirm the decryption, it is enough to click the Decrypt button or use the Enter key.
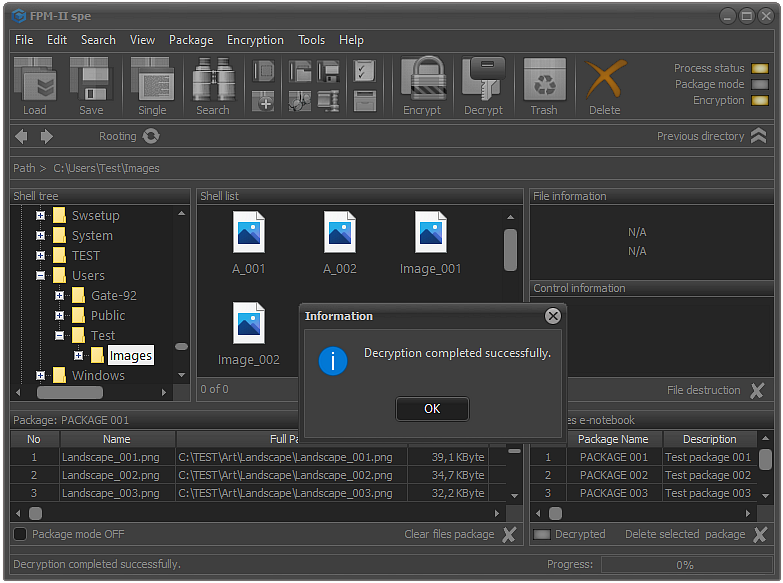
Fig.8. Completing the decryption process.
If the decryption process has passed without any errors, the system will display a message about the successful completion of the decryption of the selected files and folders.
After the decryption of the selected files and folders is completed, the files will not only be restored to their original form and usable, but their CRC and hash functions will be identical to the original ones.
This is one of the criteria that allows not only to control the decryption process, but is also a basic criteria for whether any changes have been made to the files.
Example:
Let's decrypt the file that was encrypted in the previous example and analyze the results.
What needs to be done is to configure the cryptomechanism so that it is identical to the one used to encrypt the file. For this purpose, we will choose the following cryptographic primitives:
- Cipher algorithm - Blowfish
- Crypto mode - OFB
- Hash function - Tiger
In this case, the hash salt and cipher IV are irrelevant. The system will automatically perform the necessary actions to decrypt the file.
The parameters of the file before and after decryption are as follows:
FILE DETAIL INFORMATION
| Property | Value |
|
File name |
Image_001.jpg |
| File size | 103,6 KByte |
| File path | C:\Users\Test\Images\ |
| Root | C:\ |
| Create date | 2022-12-15 12:51:38.134 ms |
| Last access | 2022-12-16 13:24:17.029 ms |
| Last write | 2022-12-16 13:24:15.988 ms |
| File CRC 8 | B6 |
| File CRC 16 | DE 43 |
| File CRC 32 | DA 8D 35 |
| File CRC 64 | A4 33 AE 28 |
| File hash | 32 80 4F D0 77 7B B3 CF CB 96 72 21 42 A0 90 44 6E A6 FC ... |
FILE DETAIL INFORMATION
| Property | Value |
|
File name |
Image_001.jpg |
| File size | 103,6 KByte |
| File path | C:\Users\Test\Images\ |
| Root | C:\ |
| Create date | 2022-12-15 12:51:38.134 ms |
| Last access | 2022-12-16 13:23:10.740 ms |
| Last write | 2022-12-16 13:21:01.450 ms |
| File CRC 8 | B3 |
| File CRC 16 | B2 C1 |
| File CRC 32 | 62 99 84 |
| File CRC 64 | B2 FA 5A 09 |
| File hash | FB 1C A9 BE 12 13 AE 5F 7B 3F EE 21 AF 21 7A 29 B4 15 EE ... |
As can be seen from the applied results after decryption, the CRC and file hash functions match those of the file before it was encrypted.
An absolute match of these values proves that no action has been taken against the file to modify the contents.
Contents